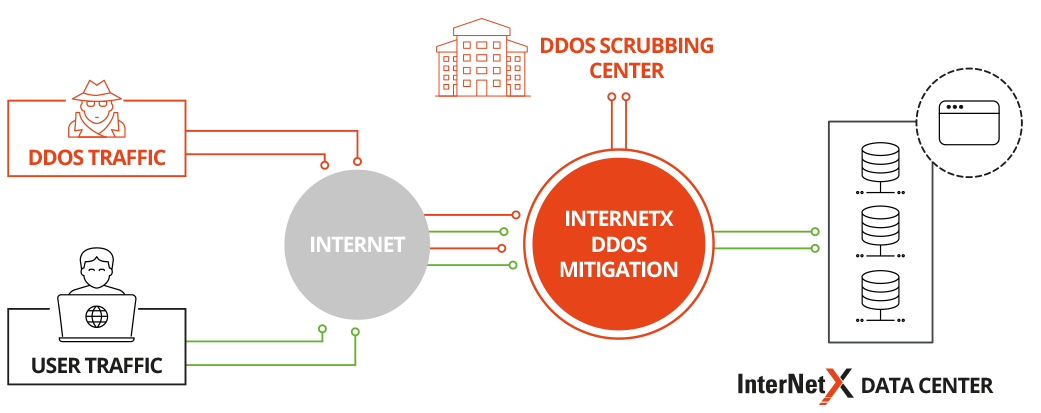
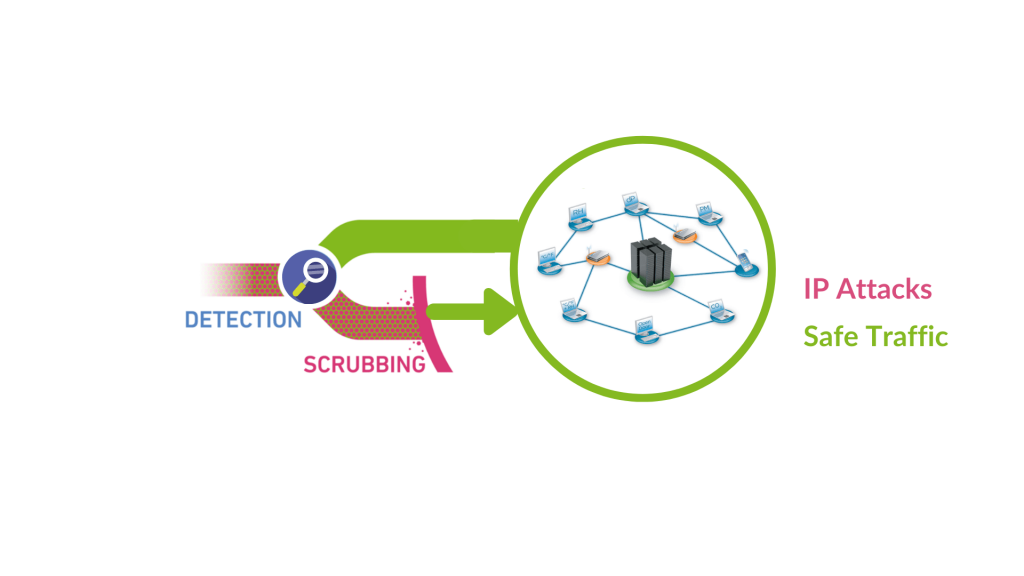
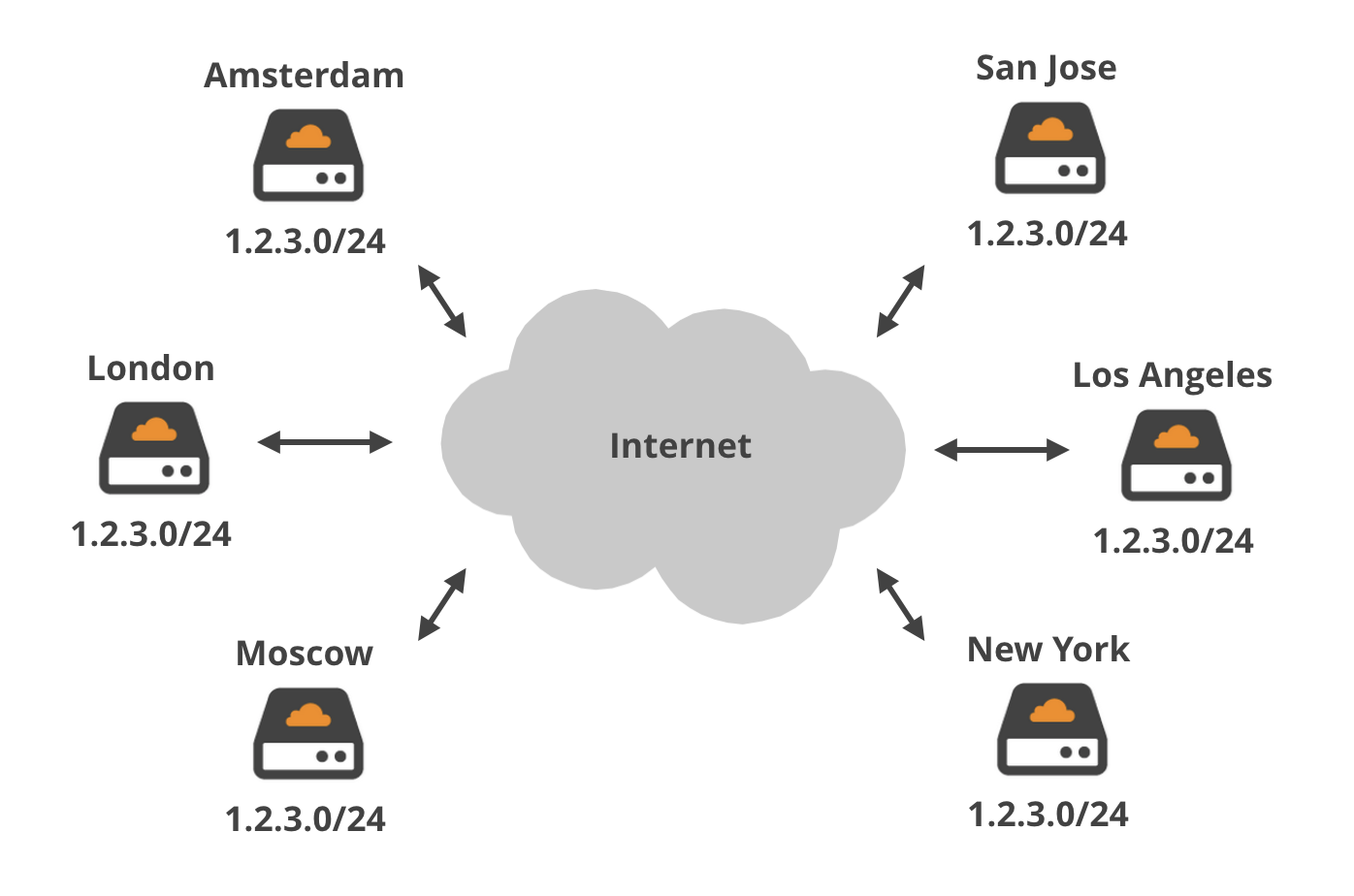
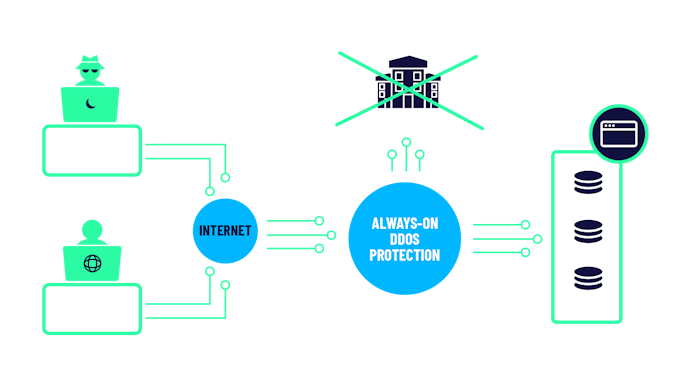
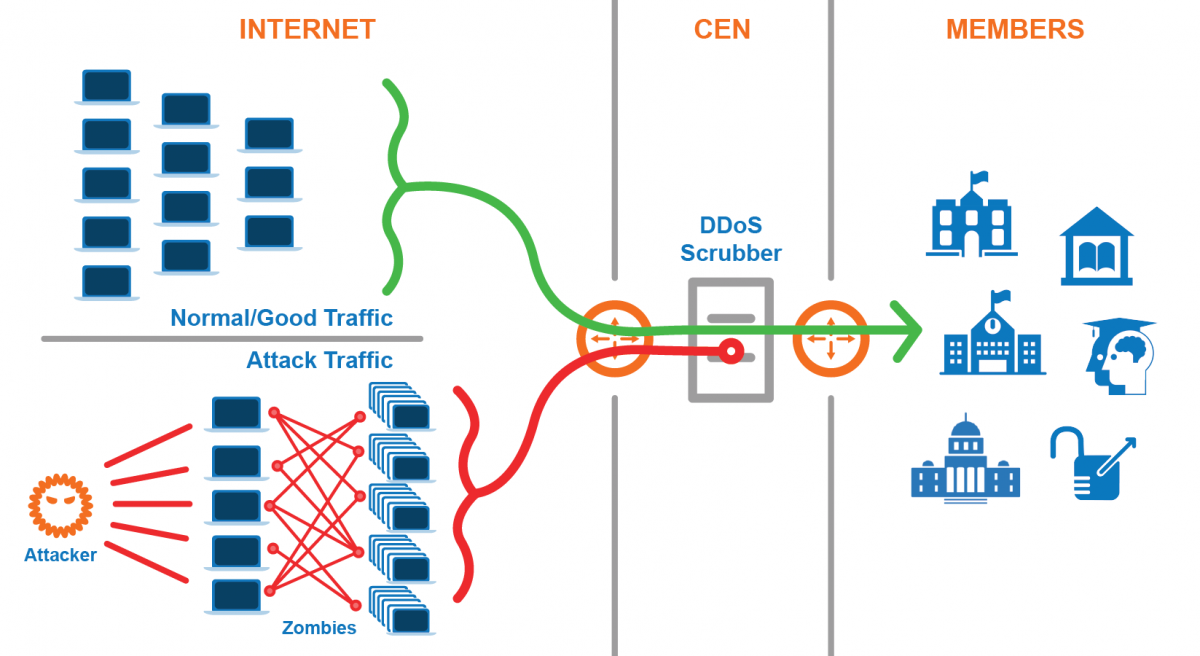
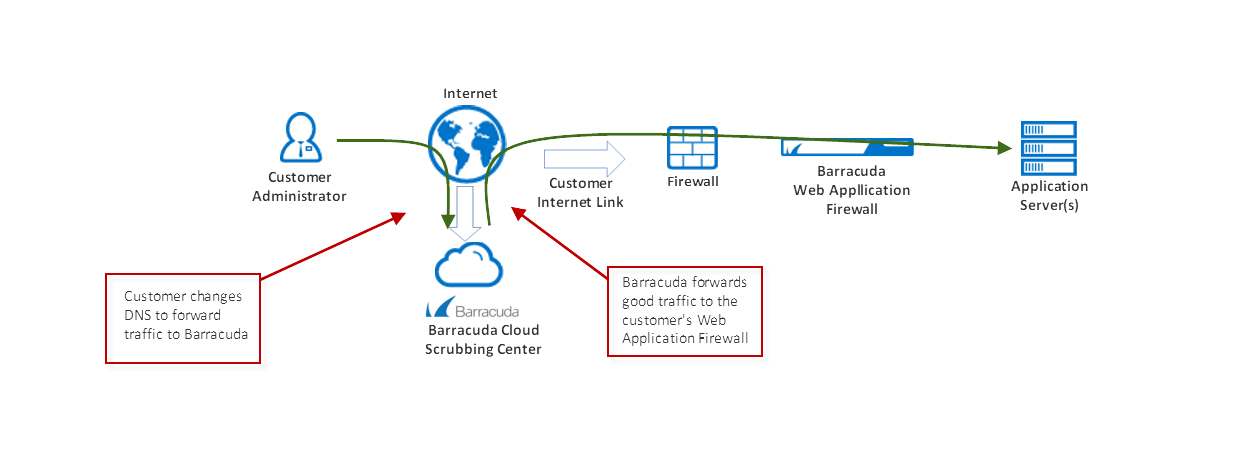
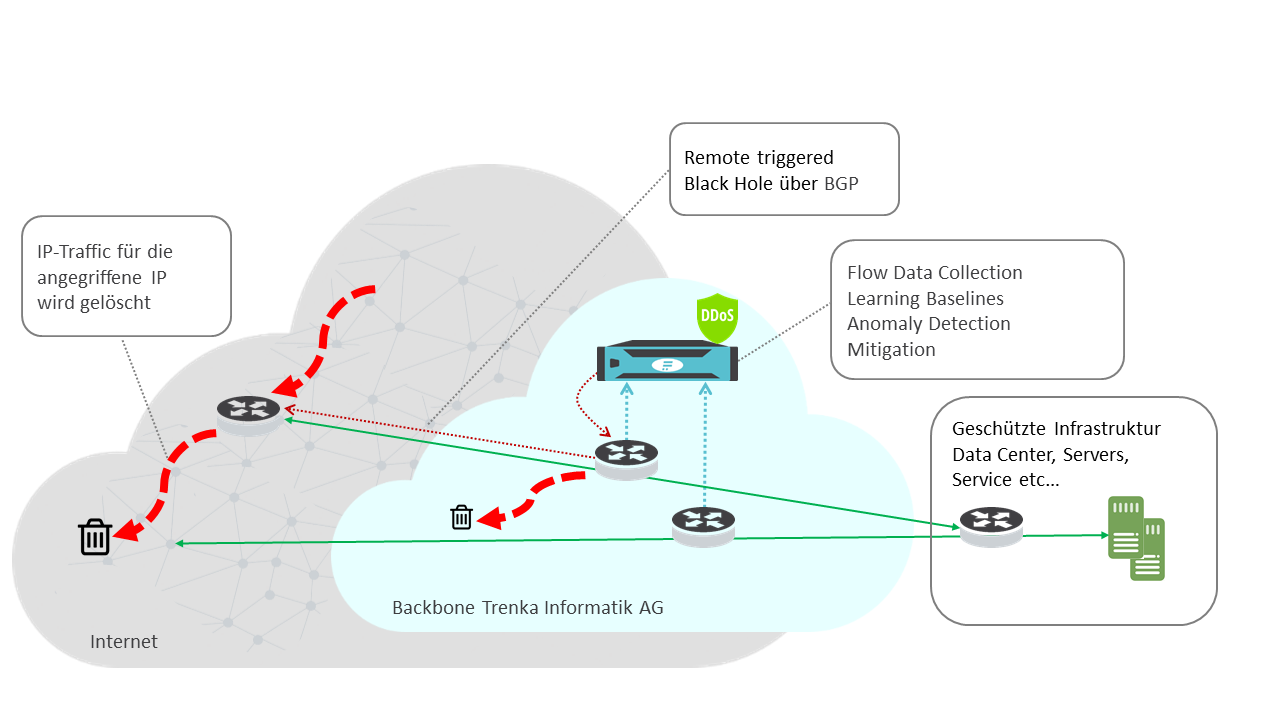
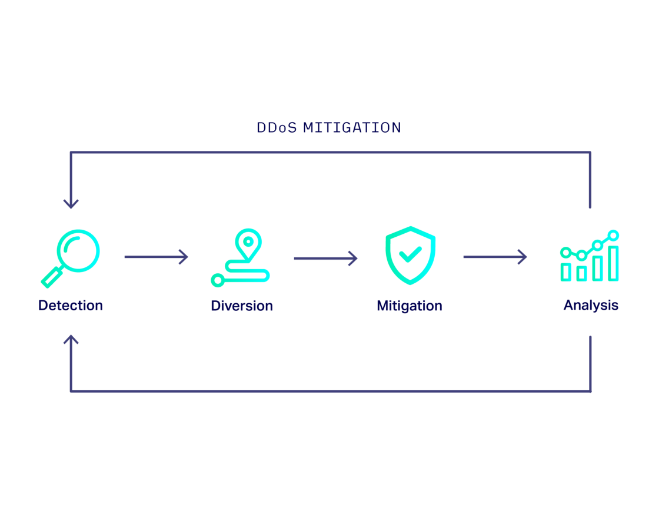
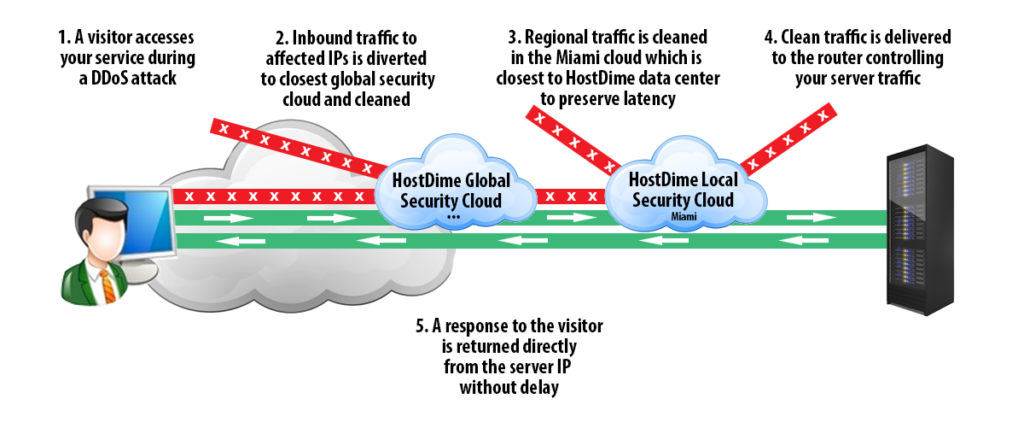
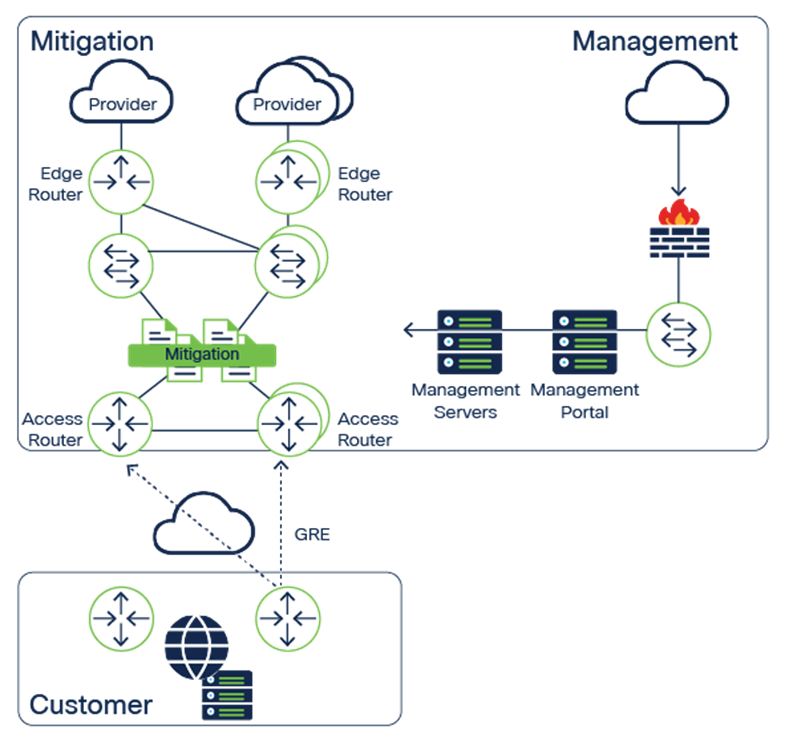
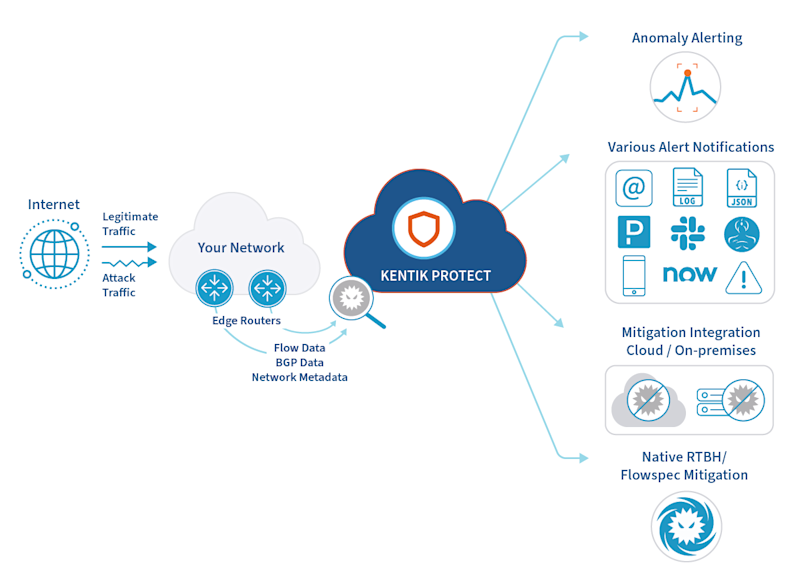
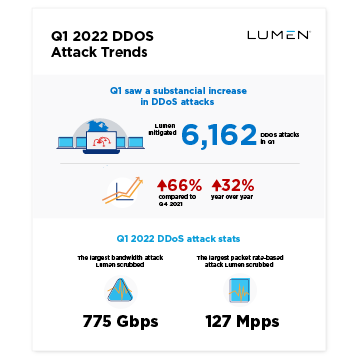
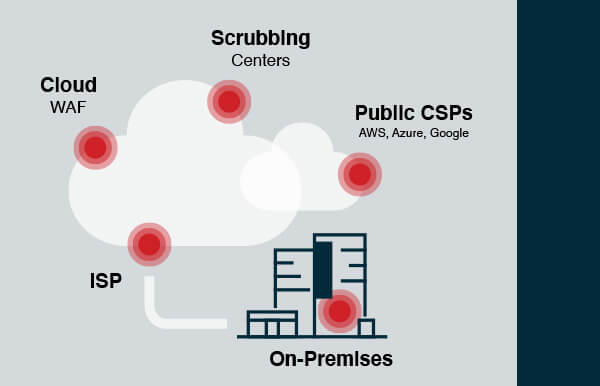
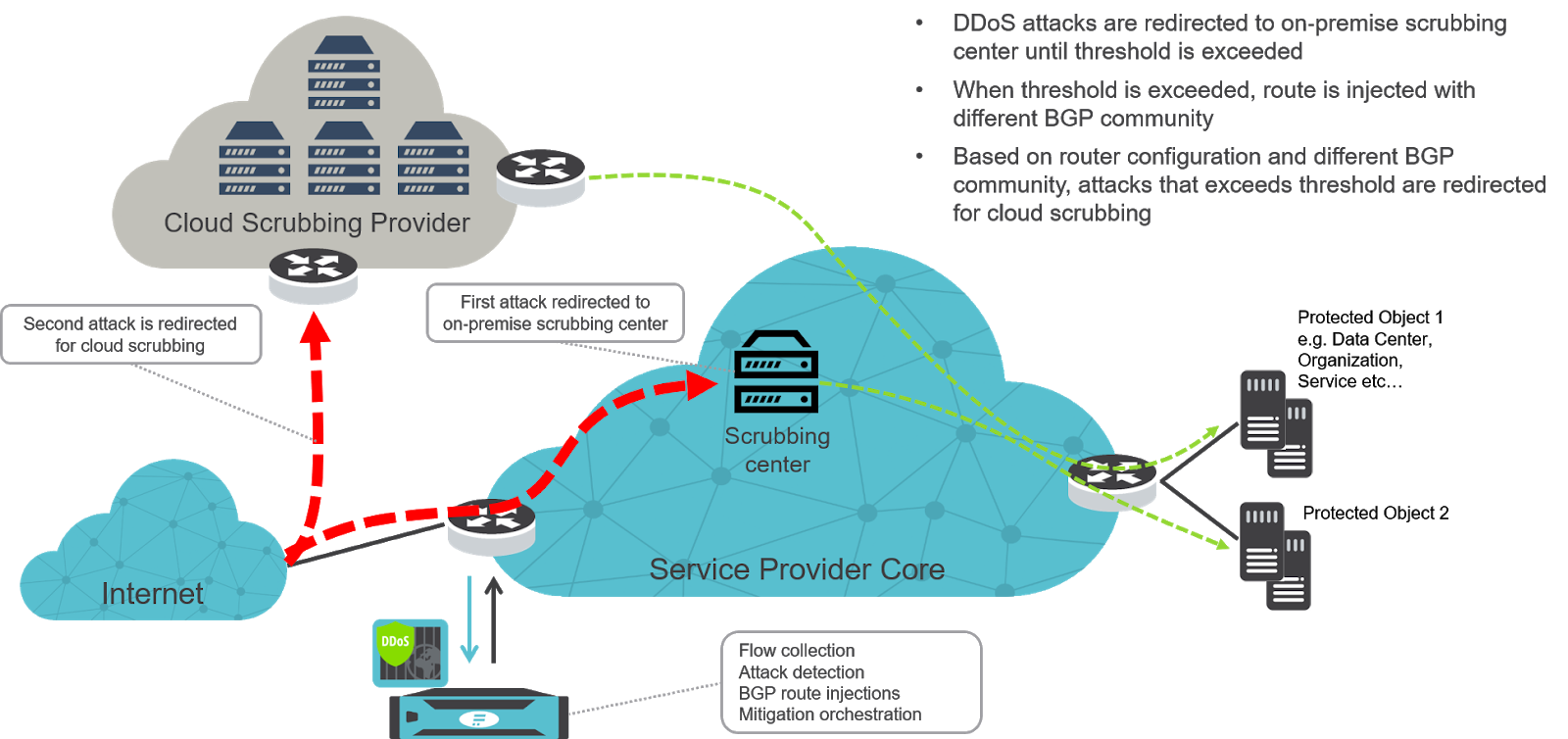
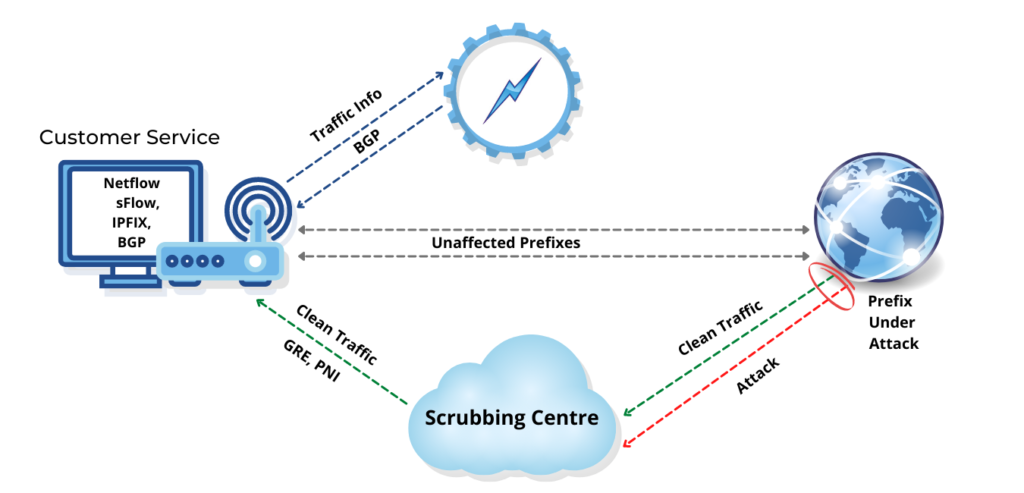
Nexusguard - Our #MX7000 Mitigation Platform is a powerful, versatile “cloud-in-a-box” #DDoS mitigation solution. When attacks threatens to overwhelm local capacities, our globally distributed scrubbing kicks-in, stopping global attacks close to its

Source address prefix filtering is a technique best used as part of... | Download Scientific Diagram
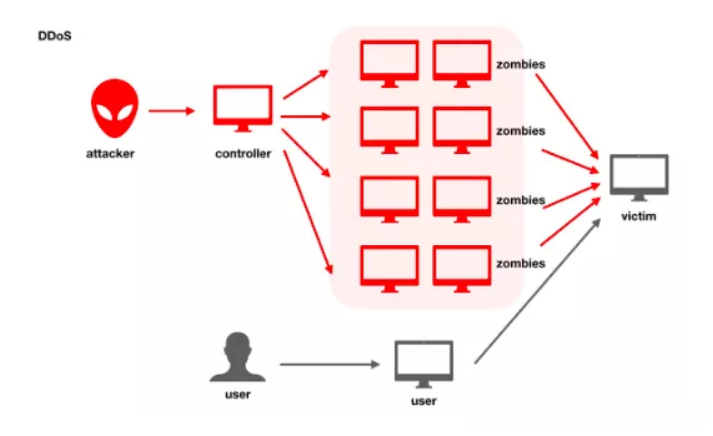
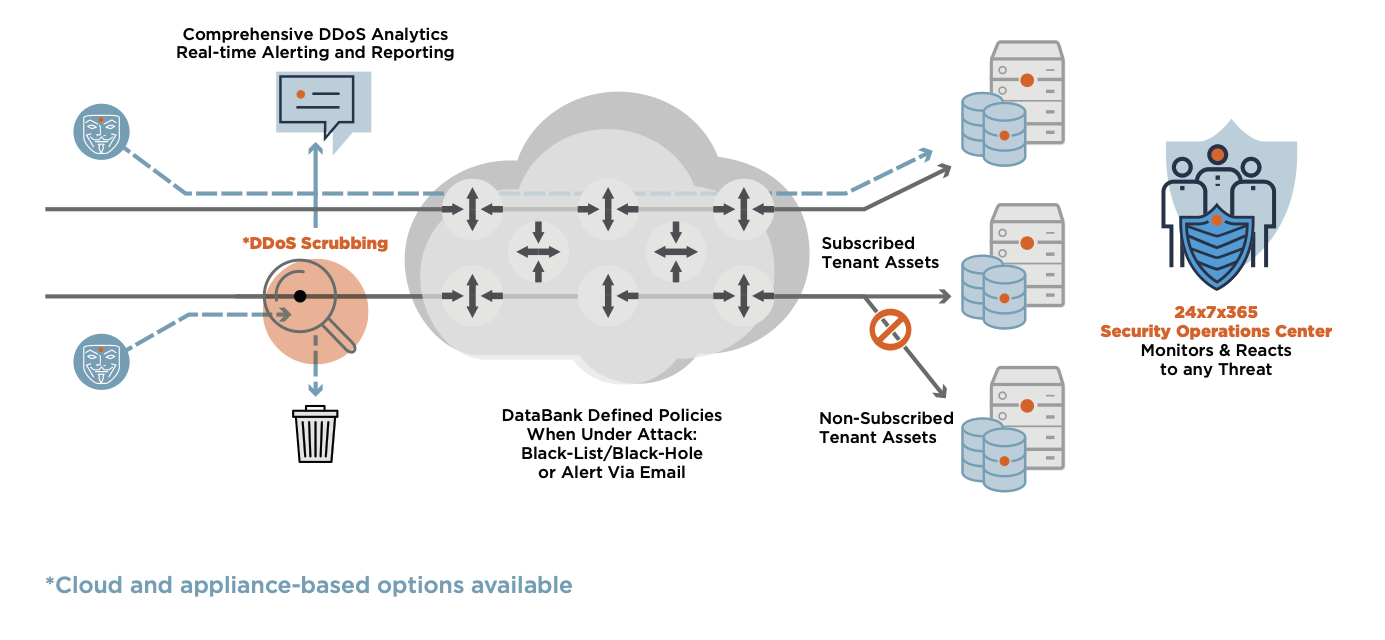
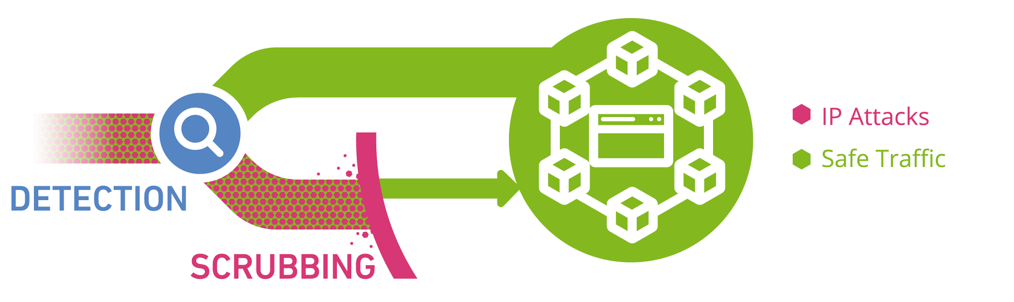
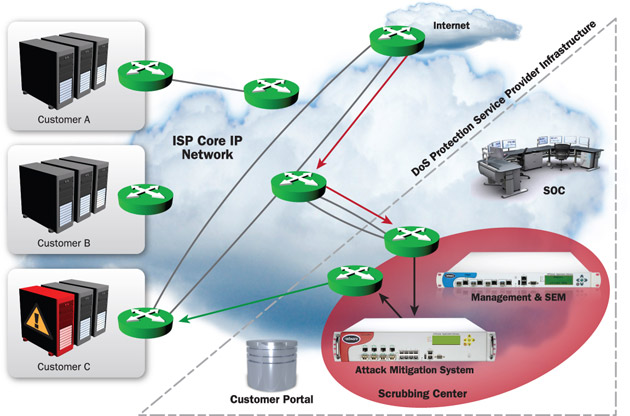
![DDoS scrubbing centers - Advanced Infrastructure Penetration Testing [Book] DDoS scrubbing centers - Advanced Infrastructure Penetration Testing [Book]](https://www.oreilly.com/api/v2/epubs/9781788624480/files/assets/ab19a836-b9b6-40b0-90cb-7012371584ab.png)